Rumored Buzz on Aws S3 Backup
Wiki Article
Get This Report about Rto
Table of ContentsThe 10-Minute Rule for Data ProtectionThe Greatest Guide To Aws Backup9 Easy Facts About S3 Backup DescribedIndicators on Ransomware Protection You Should KnowThe Basic Principles Of Protection Against Ransomware
Preserving numerous suppliers and also systems in addition to typical computer has put terrific strain on IT divisions. Moving forward, data protection need to be able to adapt to these already complex scenarios. Data security approaches are developed to secure data, maintain privacy and also protect against information loss as well as corruption without trading them for analysis as well as testimonial.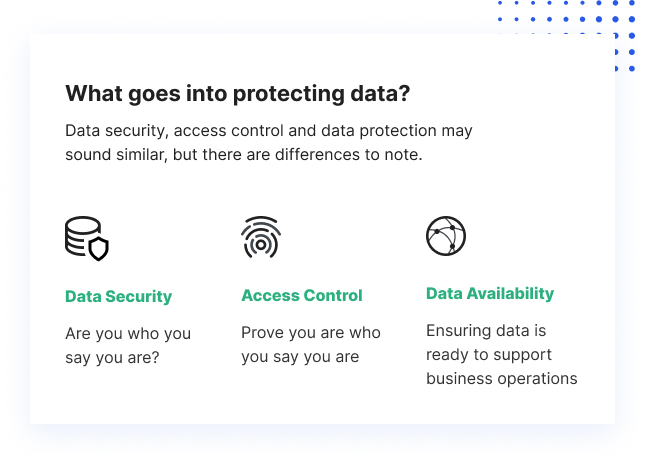
Information erasure strategies additionally verify the data can not be recovered. Access administration regulates make certain information honesty by limiting access to digital assets.
So a lot of the globe's interactions and company occurs in the cloud or with personal gadgets in remote work atmospheres. The ideal data security solutions combine robust safety and security steps with human processes and workflows. The general objective: to ensure data defense is taken into consideration early throughout the digital information life cycle.
What Does Aws S3 Backup Mean?
Information protection is every person's service, so, it's likewise essential to guarantee regular, ongoing security awareness training is component of your data protection strategy. Information privacy defines that has access to data, while information defense provides devices as well as policies to really restrict access to the data.It plays a crucial function in business operations, growth, and financial resources. By shielding information, companies can prevent information breaches, damages to reputation, and also can better fulfill governing needs. Data security remedies rely upon innovations such as information loss prevention (DLP), storage space with built-in information protection, firewall softwares, file encryption, as well as endpoint security.
It is often also called data safety and security. A data security method is vital for any organization that gathers, takes care of, or shops delicate information. A successful method can help avoid data loss, theft, or corruption and also can help lessen damage caused in case of a violation or calamity. Data protection concepts help protect information as well as make it readily available under any type of scenarios.
Little Known Facts About Rto.
Here are vital data monitoring elements relevant to data defense: making certain individuals can access and make use of the data called for to carry out organization even when this data is shed or damaged. includes automating the transmission of vital information to offline as well as on the internet storage space. involves the evaluation, cataloging, and security of details assets from different sources, consisting of center failures and disruptions, application as well as customer mistakes, device failure, and also malware and infection assaults.Data privacy is typically applied to personal health details (PHI) and also directly recognizable info (PII). Information personal privacy problems apply to all sensitive information that organizations take care of, consisting of that of consumers, investors, as well as workers.
It stops crooks from being able to maliciously use data and also assists guarantee that organizations fulfill regulative demands. Data defense policies govern just how specific information kinds are gathered, transmitted, and also made use of. Individual data includes various sorts of details, consisting of names, photos, e-mail addresses, bank account details, IP addresses of desktop computers, and biometric data.

Everything about S3 Backup
Additionally, each legislation has countless clauses that may put on one situation yet not an additional, and also all policies go through changes. This level of intricacy makes it tough to carry out compliance consistently and also appropriately. Although both information defense and also personal privacy are necessary and also both frequently integrated, these terms do not stand for the very same thing.Data privacy defines the plans that data security devices and also processes employ. Developing data privacy standards does not make certain that unapproved individuals don't have gain access to. You can restrict accessibility with information securities while still leaving sensitive data vulnerable. Both are required to ensure that information stays protected. Another vital difference between privacy as well as protection is who is commonly in control.
For protection, it depends on the companies managing data to ensure that it continues to be personal. Compliance policies reflect this distinction as well as are produced to assist ensure that individuals' privacy demands are enacted by firms. When it pertains to securing your data, there are several storage space and monitoring choices you can pick from (protection against ransomware).
Here are several of the most generally utilized practices as well as modern technologies: a very first step in information security, this entails discovering which data sets exist in the organization, which of them are business essential as well as which has delicate data that could be subject to compliance laws (s3 backup). a set of methods and also tools that you can utilize to avoid data from being stolen, lost, or inadvertently deleted.
Our Aws Backup Diaries
modern-day storage space tools offers built-in disk clustering as well as redundancy. For instance, Cloudian's Hyperstore supplies approximately 14 nines of toughness, inexpensive making it possible for storage of big quantities of data, as well as fast access for marginal RTO/RPO. Discover more in our guide to. creates copies of data and also shops them separately, making it possible to bring back the information later on in case of loss or modification.Report this wiki page